Source : Distrowatch.com
Distrolove is our love towards Open-Source OS Linux , world fines OS Try atleast once
Sep 11, 2012
PUREOS 6.0 released with GNOME 3
Source : Distrowatch.com
Jul 9, 2012
Validate an E-Mail Address with PHP, complete script
 This tutorial will teach you how to validate a e-mail id using regular expression to control email Spam. In this tutorial I used ternary operator to filter the values coming from the input box and avoid errors.
This tutorial will teach you how to validate a e-mail id using regular expression to control email Spam. In this tutorial I used ternary operator to filter the values coming from the input box and avoid errors.Complete Coding is here
$email=(isset($_POST['email']))?trim($_POST['email']):'';
function verify($email){
if(!preg_match('/^[_A-z0-9-]+((\.|\+)[_A-z0-9-]+)*@[A-z0-9-]+(\.[A-z0-9-]+)*(\.[A-z]{2,4})$/',$email)){
return false;
} else {
return $email;
}
}
if(isset($_POST['submit'])){
if(verify($email)){
echo $email." is a valid E-mail ID";
} else {
echo $email." is an invalid E-mail ID";
}
}
?>
<form action="" method="post">
<input type="text" name="email" value="<?php echo $email;?>"/><br/>
<input type="submit" name="submit" value="validate" />
</form>
Source: http://html5planet.blogspot.in/2012/07/validate-e-mail-address-with-php.html
Jun 11, 2012
Play With Xampp on linux 32 bit and 64 bit OS
In Previous blog , I just taught you how to install Xampp on 32 bit and 64 bit distro , in this tutorial I am going to tell you how to make web development easy on Linux. When you work on Linux environment everything is not easy as it is stable and secure , you have to come up with lots of issues and how to solve it.
Problem no.1
How to give write permission to /htdocs to create folder and files?
This is one of biggest issue after installing xampp as we have to create .php files under /htdocs folder
solution : Its not a rocket science to give write permission to a folder .
open terminal
Note if you use KDE then use su command else use sudo.
after opening terminal write
=========================================
=========================================
Problem no.2
Which editor will be best?
solution: If you want dreamweaver like editor then kompozer will come closer ,if you want fast and stable editor there is numeros my personal favorite are
- kate
- geany
- gedit (you have to twaeked it)
- bluefish
- kompozer
Problem no. 3
Which browser will be better?
solution : I prefer Firefox over any browser and don't know why. You can work with any browser of your choice . My top 5 browser are
- firefox
- chrome
- opera
- safari
- konqueror
May 25, 2012
Launching tasks when computer is idle
DistroWatch answers: It is possible to check how busy your CPU is and run certain programs when the processor is idle. However, this may not be the best solution if your goal is running programs without having them interfere with system performance. First, let's look at how to run a command when the CPU is relatively idle. There are a few ways to check to see how busy the CPU is, but one of the easiest is using the uptime command:
jesse@drew:~$ uptimeThe uptime program shows us the current time, how long the computer has been running, how many users are logged in and the processor's load average. The load average tells us how busy the CPU is. The uptime program displays three numbers for load averages, the first shows us how busy the CPU has been, on average, for the past minute, the second number indicates average processor load for the past five minutes and the third number indicates load for the past fifteen minutes. A load average of 1.00 would mean the CPU is constantly busy, a load of 0.00 would indicate the machine is practically idle. If we want, we can set a job to run only if the load average falls to a certain point, say 0.01. The following script checks the system load once a minute and, when the load drops below 0.05, it will run a job, provided on the command line, for us:
15:40:49 up 8:17, 3 users, load average: 0.92, 0.88, 0.85
#!/bin/bashNow there are problems with this approach. One being that we're constantly running checks, which is a little wasteful. Another is that if our load average never drops below 0.05 our task doesn't get to run. Another issue is that if we want to use the computer while our intensive task is running we either have to interrupt it or deal with reduced performance while our important job is running. In my opinion a better way to handle the situation is to run our special task whenever we want, but make sure it does not affect system performance.
if [ $# -lt 1 ]
then
echo usage $0 command
exit 0
fi
load=`cat /proc/loadavg | awk '{print $1*100}'`
while [ $load -gt 5 ]
do
sleep 60
load=`cat /proc/loadavg | awk '{print $1*100}'`
done
$@
One command useful for keeping jobs out of the way is nice. The nice command tells the operating system to assign a lower priority to our job. The lower priority will help to keep the job from using the CPU while other, higher priority tasks, are active. Here is an example of the nice command in action, being used to run the apt-get program:
nice apt-get updateShould a job already be running and we want to lower its priority, making it less intrusive, we can use the renice command. The renice command typically accepts two pieces of information, the new priority we want to assign and the process ID of the job we want to alter. Priority numbers are typically set in the range of -20 to 19, with 19 being the lowest possible priority. The following command assigns the lowest priority to process 3175:
renice -n 19 -p 3175While the nice and renice commands work on adjusting the priority of jobs in the CPU sometimes we find that the main bottle neck to performance is with the hard drive. For instance backup processes require a lot of disk access and we might want to keep them out of the way. For these sorts of tasks we have the command ionice. The ionice command works much the same way as nice and renice. With ionice we can either launch a new task with altered priority to the disk or we can make adjustments to processes already running. The ionice command recognizes three classes of priority: realtime (which is the most aggressive), best-effort (which is the default) and idle (which should not interfere at all with other tasks trying to access the disk). The ionice manual page tells us to make a process idle, we assign it a class of 3. In the following example we perform a backup using a polite, idle, disk priority:
ionice -c 3 tar czf mybackup.tar.gz ~/DocumentsIn this next example we tell the system to make sure the process with ID 4571 takes the lowest priority when accessing the disk:
ionice -c 3 -p 4571Should we wish to, we can use both the ionice and renice commands to make sure our job stays out of the way both when accessing the CPU and the disk. This next example begins a backup of our Documents directory and assigns the process both a low disk and low CPU priority:
ionice -c 3 tar czf mybackup.tar.gz ~/Documents &The above commands -- nice, renice and ionice -- affect the scheduling and priority of a task. There is another command, called CPUlimit, which throttles a process. (CPUlimit is usually not installed by default, but is available in many Linux repositories.) What's the difference between throttling and scheduling? Well, a task with a low priority can still use 99% of the CPU if nothing else is competing for system resources. The low-priority task only backs off when another process wants to step in. Throttling a process, on the other hand, forces that process to only use a limited per cent of the available CPU. We can limit a process to use only 10%, 20%, 50%, etc of the CPU, whether the machine is idle or busy. The CPUlimit command typically takes two pieces of information, a process ID of the job we want to throttle and the maximum percentage of the CPU we want to allow to the process. For example, the following limits the process 6112 to using just 25% of our CPU:
renice -n 19 -p $!
cpulimit -p 6112 -l 25The following commands start a new backup job and then throttles its CPU usage to 10%:
tar czf mybackup.tar.gz ~/Documents &
cpulimit -p $! -l 10 -b
Source : http://distrowatch.com/weekly.php?issue=20120521
May 6, 2012
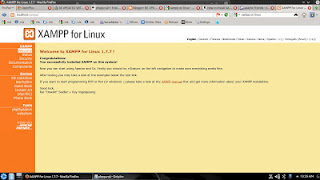
Install XAMPP on 64 bit Linux Distro
LAMPP: Starting Apache...
Read complete tutorial at Cellguru
Mar 26, 2012
5 Tips and Tricks for Using Yum

If you're using one of the Fedora/Red Hat derived Linux distributions, odds are you spend some time working with Yum. You probably already know the basics, like searching packages and how to install or remove them. But if that's all you know, you're missing out on a lot of features that make Yum interesting. Let's take a look at a few of the less commonly used Yum features.
Yum comes with a lot of different distributions, but I'm going to focus on Fedora here. Mainly because that's what I'm running while I'm writing this piece. I believe most, if not all, of this should apply to CentOS, Red Hat Enterprise Linux, etc., but if not, you may need to check your man pages or system documentation.
Working with Groups
If you use the PackageKit GUI, you can view and manage packages by groups. This is pretty convenient if you want to install everything for a MySQL database or all packages you should need for RPM development.
But, what if you (like me) prefer to use the command line? Then you've got the group commands.
To search all groups, use yum group list. This will produce a full list of available groups to install or remove. (Yum lists the groups by installed groups, installed language groups, and then available groups and language groups.)
To install a group, use yum group install "group name". Note that you may need quotes because most group names are two words. If you need to remove the group, just use yum group remove "group name".
Want to learn more about a group? Just use yum group info with the group name.
Love the Yum Shell
If you're going to be doing a lot of package management, you want to get to know the Yum shell.
Just run yum shell and you'll be dumped in the Yum shell. (Which makes sense. It'd be weird if you got a DOS prompt or something...) Now you can run whatever Yum commands you need to until you're ready to exit the Yum shell.
For instance, want to search packages? Just type search packagename.
install or remove, Yum will not complete the transaction immediately. You need to issue the run command to tell Yum to do it. This gives..............Read more at linux.com
Mar 20, 2012
Simple command-line tricks

It has been a while since we had a column dedicated to useful command line tips. This week we will cover some simple, but often useful, command line tricks.
This first command will play all of the MP3 files in my Music directory, including all of the files found in sub-directories. It uses the find program to locate all MP3 files in the music directory and passes them off to the mplayer multimedia program to be played. The "-iname" flag tells find to ignore the case of the file name so that myfile.mp3 will be treated the same as MyFile.MP3. The braces, {}, toward the end of the command represent a file located by the find program which will be handed over to mplayer.
find ~/Music -iname "*".mp3 -exec mplayer {} \;Sometimes people send me archives or CDs which contain files with improper access permissions. The first of the following two commands locates all folders in the current directory and grants my user full access to them. The second command locates all files in the current directory (and sub-directories) and provides read and write access to them without making them executable. The "-type" flag lets us select whether we are operating on a (d)irectory or on a (f)ile. The chmod program then applies the proper permissions to each directory and file.
find . -type d -exec chmod 700 {} \;When we first install our operating system we sometimes need to change the system date. Or, if our computer clocks don't automatically change to accommodate daylight saving time we might need to make adjustments. From the command line this is fairly straight forward. The following command sets the current system time to noon.
find . -type f -exec chmod 600 {} \;
date -s "12:00"Please note we will need to have administrator access to change the date and time. The next command tells the machine to change the clock to March 24, 12:30.
date -s "Mar 24 12:30"They say timing is everything and it is useful to be able to schedule commands to be run at a later point in time. The following command will cause the sound file alarm.wav to play at 5pm.
echo mplayer alarm.wav | at 17:00The at command can also be used to run scripts at a given time as in the following example where we run my_script at 11:40.
at 11:40 < my_scriptLast, but not least, this is a very handy command to have when an application needs to be terminated. Let's say we have the VLC multimedia player running and, for some reason, we need to close it. Rather than look up its process ID and terminate the program with the kill command we can use a program called pkill to shut down the process by name.
pkill vlcThe command line is very flexible and often useful, not only for complex tasks and processing information, but also for common day-to-day activities.
Source Distrowatch.com
Mar 18, 2012
Linux Tutorial -Using the Secure Shell
Secure shell, specially the OpenSSH implementation of secure shell, is an important and valuable tool. This holds true largely because of the security it provides us for common tasks, but also because OpenSSH is so portable, enabling it to function on most modern operating systems. OpenSSH was originally forked from OSSH and developed for the OpenBSD operating system. Since its début in 1999, OpenSSH has been ported to Linux, to other BSD projects and to proprietary operating systems. Chances are if you're reading this from an open source operating system you have an OpenSSH component installed.
What's so important about OpenSSH? It used to be most network services sent their data in plain-text, completely open for anyone to read. While this was fast and convenient (and easy to debug) it wasn't secure. Logging into a remote machine meant sending usernames and passwords over the lines without hiding them in any way and transferring files in the open made it fairly easy to intercept them. OpenSSH encrypts its traffic, preventing people from listening in and gathering your login credentials or copies of any files you're sending over the network.
All of this may sound a bit abstract so I'd like to share a handful of examples of how OpenSSH can be used to communicate with a remote machine. In the following examples I'll be communicating with a remote server named "harold". For these examples to work the remote machine, harold, must be running the OpenSSH server and be able to accept connections on port 22.
Perhaps the most common usage of OpenSSH is logging into a remote machine to run command-line programs. System administrators often perform updates, check logs and change configurations this way. To do this we run
ssh harold
The above example is secure shell invoked in its most simple form. Should we be connecting to a server where our username is different than our username on the local machine we can use the "-l" option. For example, if we wish to login to the remote machine as the user "susan" we would run
ssh -l susan harold
In both cases presented above we will be prompted for a password and then given a terminal prompt on harold. When we are finished working on the remote server we can run "exit" to return to working on our local machine.
Another common usage of OpenSSH is the transfer of files between computers. There are two ways to do this. The first is to set up an interactive connection to the remote machine using the sftp command. A sftp session works much the same way as plain FTP, providing an interactive experience, but sftp encrypts the traffic between the machines, including our password. To start a secure file transfer session we use
sftp harold
Alternatively, if we have a different username on the remote host, we can use
sftp susan@harold
When using sftp we terminate the secure session using the "quit" command. If you're not familiar with using command line file transfer programs, there are graphical clients, such as gFTP or Filezilla, that make the process more intuitive. Another way to transfer files is with the secure copy command, scp. The scp command works much the same way as the "cp" command line program, but with the ability to work over a network. In the following example we copy a file, test_file.txt, to our home directory on harold.
scp test_file.txt harold:test_file.txt
As with ssh and sftp we can send data to the remote machine as another user:
scp test_file.txt susan@harold:test_file.txt
In other instances we may wish to copy files to a remote directory besides our home. In those cases we can specify the directory we want to use after the server name. This example copies our text file to our Work directory on the remote computer:
scp test_file.txt harold:/home/jesse/Work/
The scp command works the other way too, allowing us to copy remote files to our local machine. In this example we copy a text file from harold and save it in our current working directory.
scp harold:test_file.txt local_copy.txt
Sometimes administrators find themselves wanting to perform the same commands on multiple remote machines. There is a handy tool called ClusterSSH which will connect to several remote servers and send commands we type once to each machine. Bill Childers has a good tutorial on setting up and using ClusterSSH. I recommend reading it if you find yourself managing multiple machines.
Mar 14, 2012
Indian Railway Budget (रेल बजट) 2012
Indian Railway Budget 2012
On his Speech Travedi Said
- Emphasis will be on better Railway infrastructure.
- Railway Security is our prime concern
- Gross budgetary support of over Rs 7.35 lakh crore for Railways
- Rs.5.60 lakh crore required for modernization
- Railways to grow at 10% annually
- Annual Plan for Railway for 2012-13 is at highest ever Rs 60,100 crore
- Propose Rail Regulator to enhance Security
- Anil Kakodkar to head new railway safety authority
- Urgent need to connect to northeast and J&K
- Target should be zero death
- Aim to upgrade 19,000 km of tracks in five years
- Pending Projects is 487 lack of funding
- 85 new line projects to be introduced
- Electrifications of 6500 kms
- 1000 new Railway Stations
- Collective responsibility of Indian Parliament to make the Railways to be the best in the world
- upgrading technology to increase speed of trains
- Train will run @ 160km/hr
Mar 11, 2012
Linux Mint 12 LXDE
Who Should USE
- Beginners
- Who Want Fast Desktop
- Old harware
Screenshot of Linux Mint 12 LXDE :
System requirements for Linux Mint 12 LXDE
- x86 processor
- 256 MB RAM
- 3 GB of disk space
- Graphics card capable of 800×600 resolution
- CD/DVD drive or USB port
Installation is simple just download the iso image and burn to CD or create LIVE USB using software
'Startup Disk Creator' or 'UNetbootin'.
Download ISO Platform : 32 bit Size : 657M
Quick Review :
Its damn fast ,detected all hardware of my laptop Acer Emachine E732Z, till now not a single crash, it will be so early to say it stable as I am using for one day.
Please Share your Experiences through comments.
Jan 3, 2012
Mozilla Firefox 64 bit benchmark beats chromium 17
My Test Machine:
Acer emachines e732z
Intel dual core 2.13 GHZ
2GB DDR3 Ram
OS :OpenSuse 12.1 Gnome
Browser : Firefox 8 64 bit
Note : Result very on system , if you have faster system result will be better.
Acid test :
Now firefox got 100% in this test ,improving its previous record 97%
Sunspider :
Content Version: sunspider-0.9.1- excellent 297.9ms
Opera's 11.52 64 bit result were very close
============================================
RESULTS (means and 95% confidence intervals)
--------------------------------------------
Total: 320.7ms +/- 1.2%
--------------------------------------------
chromium 17 64 bit was 378.44ms
Google's V8 benchmarch
Firefox Score
DeltaBlue: 3435
Crypto: 5492
Read More